Autonomous Cyber Defense
Military-Grade Protection. Fully Autonomous.
AI agents that detect, respond, and evolve—without human intervention. For families. For businesses. For those who can't protect themselves.
%20(1).avif)
Defend What Matters
Protection that fits your world. Choose your path.
Our Mission
Aktoh is built by Americans to protect those who cannot protect themselves. Whether due to cost or knowledge gaps, too many are left vulnerable—children targeted and exploited, businesses drained by fraud, with that stolen money funding crime and our nation's enemies.
The cyber world has always been criminals innovating while defenders sprint to catch up. We flipped the script. We study malware, engage with malicious actors, and learn their methods firsthand—so we can build defenses that don't just respond. They anticipate.
We believe everyone deserves a safe, secure online environment. Our mission is to make that a reality.
We believe everyone deserves a safe, secure online environment. Our mission is to make that a reality.

Innovating Cybersecurity Solutions for the Digital Age
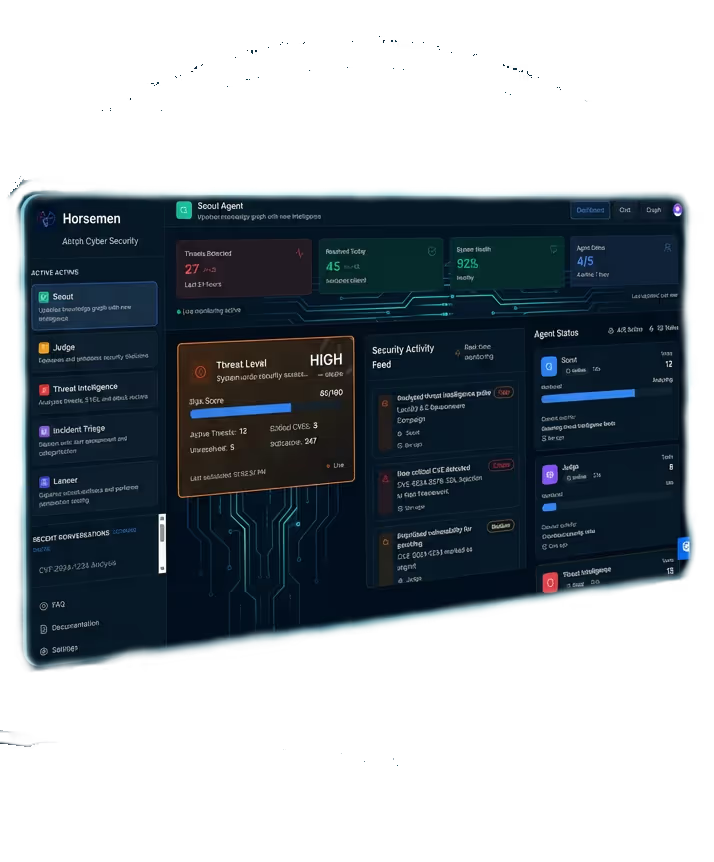
AI agents that integrate offensive, defensive, and governance operations into a single system.
Autonomous Threat Detection
Our AI agents continuously monitor, detect, and respond to threats without human intervention. Zero-day vulnerabilities are identified and remediated before they can be exploited.
Red Team & Blue Team Operations
Offensive and defensive security working in tandem. Our Red Team Agent simulates real-world attacks while Blue Team Agent provides continuous defensive monitoring and response.
Deception Technology
Sleight creates realistic decoy environments that trap attackers and safely observe their behavior—without exposing real assets. Honeytokens and fingerprinting identify threats before they reach production systems.
Self-Evolving Defense
EVOLVE continuously learns, designs, and improves agents to stay ahead of emerging threats. The system builds new tools and adapts to adversary tactics autonomously.
Adversary Intelligence & Simulation
We gather intelligence from real attacker behaviors, malware ecosystems, and dark web markets—allowing our systems to simulate, predict, and counter adversaries before they strike.
Incident Forensics & Recovery
Deep incident breakdown post-breach. Our Forensic Analysis and Disaster Recovery agents automate investigation, build incident narratives, and restore operations fast.
TESTIMONIALS
What Our Clients
Have To Say
Trusted by organizations who depend on resilient, next-generation cyber defense.
“The Protection And Guidance We've Received From AKTOH Has Been Invaluable.We're Confident In Their Ability To Protect Us From All”
“We Rely On AKTOH's Expertise To Safeguard Our Operations From Evolving Cyber Threats. Their Team Is Professional And Always Proactive.”

Satisfied Customer
8
5
3
6
9
0
8
7
4
32
.
7
9
6
3
2
0
4
7
9
6
k
Prevented Damages
8
5
3
6
9
0
8
7
4
1
10
9
6
3
2
0
4
7
9
6
mil
+
“AKTOH's Cybersecurity Services Have Provided Us With Peace Of Mind Knowing That Our Business Is Protected. They Are The Partner We Trust.”

Protection You Can Count On"
Join the organizations that trust AKTOH to defend against tomorrow's threats.
Cyber Security Insights To Protect Your World.
Explore the rise of AI-driven threats and the importance of proactive defense strategies.
Elite Defense. Limitless Security.
Defend Your Future. Secure Yours Now.
Discover how our expertise keeps your world safe, so you can focus on what matters most.








.svg)

.svg)