SLEIGHT: PROTECT YOUR FAMILY ONLINE
Trusted By Thousands Against:
PROTECTING FAMILIES • STOPPING SEXTORTION • CATCHING RANSOMWARE • BLOCKING PHISHING • REPORTING TO FBI • PRIVACY FROM BIG TECH • STOPPING IDENTITY THEFT • SMART HOME SECURITY • CATCHING SCAMMERS • PROTECTING KIDS ONLINE • BLOCKING PREDATORS • FAMILY PRIVACY • DEVICE PROTECTION • NO TECH KNOWLEDGE NEEDED • 24/7 AUTOMATIC PROTECTION • PROTECTING FAMILIES • STOPPING SEXTORTION • CATCHING RANSOMWARE • BLOCKING PHISHING • REPORTING TO FBI • PRIVACY FROM BIG TECH • STOPPING IDENTITY THEFT • SMART HOME SECURITY • CATCHING SCAMMERS • PROTECTING KIDS ONLINE • BLOCKING PREDATORS • FAMILY PRIVACY • DEVICE PROTECTION • NO TECH KNOWLEDGE NEEDED • 24/7 AUTOMATIC PROTECTION •
PROTECTING FAMILIES • STOPPING SEXTORTION • CATCHING RANSOMWARE • BLOCKING PHISHING • REPORTING TO FBI • PRIVACY FROM BIG TECH • STOPPING IDENTITY THEFT • SMART HOME SECURITY
AUTOMATED THREAT REPORTING • FBI NOTIFICATION • ISP ALERTS • PARENTAL CONTROLS • ACTIVITY MONITORING • PREDATOR DETECTION • SCAM PREVENTION • RANSOMWARE BLOCKING • IDENTITY PROTECTION • SMART HOME DEFENSE • AUTOMATED THREAT REPORTING • FBI NOTIFICATION • ISP ALERTS • PARENTAL CONTROLS • ACTIVITY MONITORING • PREDATOR DETECTION • SCAM PREVENTION • RANSOMWARE BLOCKING • IDENTITY PROTECTION • SMART HOME DEFENSE •
AUTOMATED THREAT REPORTING • FBI NOTIFICATION • ISP ALERTS • PARENTAL CONTROLS • ACTIVITY MONITORING • PREDATOR DETECTION • SCAM PREVENTION • RANSOMWARE BLOCKING • IDENTITY PROTECTION • SMART HOME DEFENSE

Every day, predators use AI to create fake profiles targeting kids on social media.
Meanwhile, scammers mimic bank emails to steal passwords and hackers break into smart home devices. Today's threats are faster, smarter, and anyone can launch them with minimal resources.
Traditional antivirus software only reacts after damage is done. Sleight works differently—it catches threats before they reach your family.
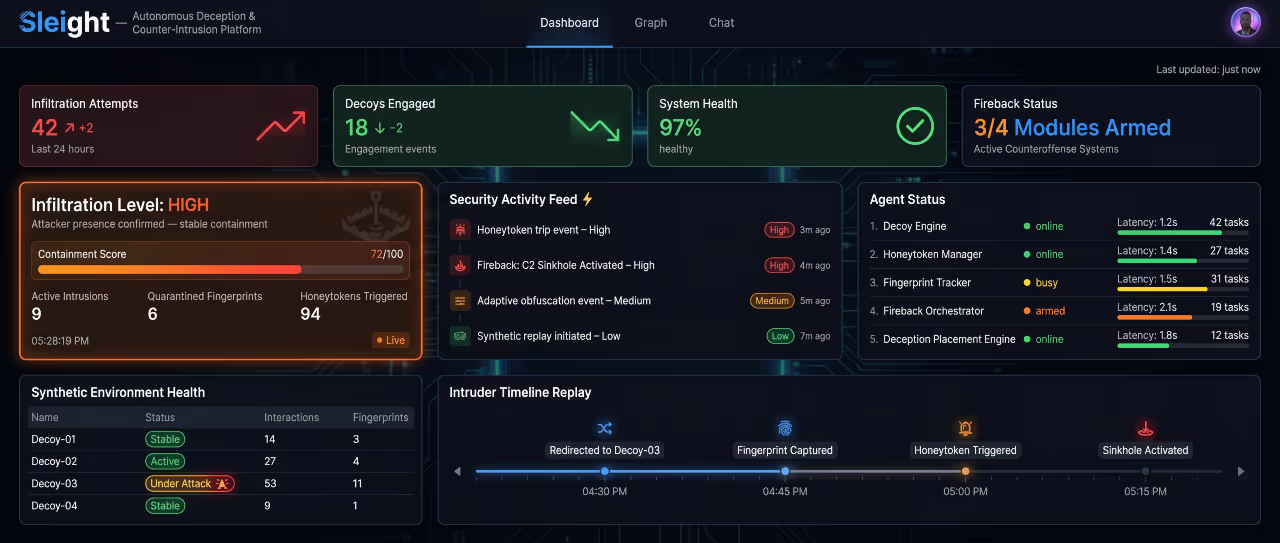
Sleight Doesn't Block Threats.
It traps them
Active decoys
Realistic traps. Zero exposure.
Attackers engage what they believe is real. Your actual environment is never touched.

THREAT CONTAINMENT
Caught and studied. Safely.
Sleight watches every move the attacker makes. Intelligently understanding their tools, tactics, and targets.
All while your real systems remain completely protected.
.avif)
CONTINUOUS LEARNING
Every threat makes you stronger.
Protection improves automatically with every threat caught. No updates to install. No settings to configure. Your defenses evolve while you go about your life.

INTELLIGENT & AUtonomous
Protection that adapts on its own
Protection improves continuously — without interrupting your daily use.

SEGMENTATION
Tools built to grow your business



Stops Threats of
Every Kind




SELECT YOUR PLAN
Deception-based cyber self-defense for individuals and families.
Advanced autonomous protection with real-time threat detection and response.
Family
What Our Clients
Have To Say
8
5
3
6
9
0
8
7
4
99
.
9
9
6
3
2
0
4
7
9
6
%
8
5
3
6
9
0
8
7
4
2
00
9
6
3
2
0
4
7
9
6
mil
+



